158.63.258.200: Risks, and Common Misinterpretations of This IP Address
In the digital world, IP addresses play a vital role in identifying devices, tracking activity, and enabling communication across networks. One such term that occasionally appears in logs, error messages, or search queries is 158.63.258.200. At first glance, it appears to be a standard IPv4 address. However, upon closer inspection, this string reveals something unusual and important. This article explores 158.63.258.200 in detail—what it is, why it appears, whether it is valid, and what it could mean for system administrators, developers, cybersecurity professionals, or curious users. If you’ve encountered this value in logs or reports, this guide will help you understand it clearly and accurately.
What Is 158.63.258.200?
The string 158.63.258.200 appears to follow the structure of an IPv4 address, which is normally written in this format:
X.X.X.X
Each section (called an octet) must contain a number between 0 and 255.
However, in 158.63.258.200, the third octet is 258, which exceeds the allowed maximum value of 255. This means:
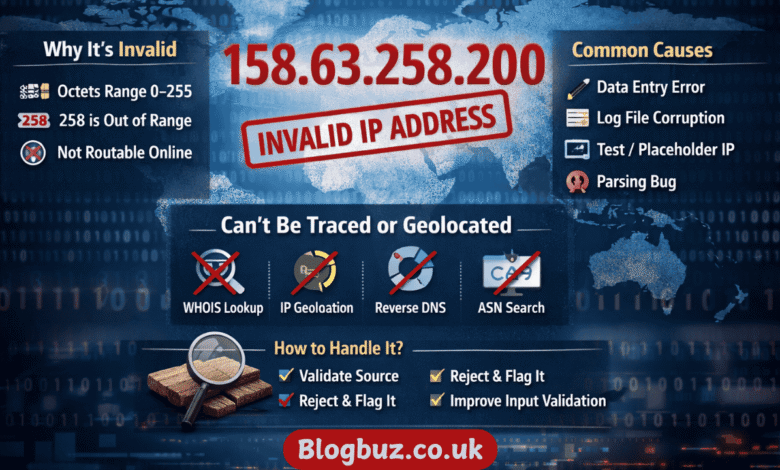
👉 158.63.258.200 is not a valid IPv4 address.
Because of this, it cannot exist on the public internet, cannot be assigned to a device, and cannot be resolved through DNS or WHOIS lookups.
Why 158.63.258.200 Is Technically Invalid
To understand why 158.63.258.200 is invalid, it helps to review how IPv4 addressing works.
IPv4 Rules:
- Total of 4 octets
- Each octet ranges from 0 to 255
- Written in decimal format
- Example of a valid IP: 158.63.25.200
Why 258 Breaks the Rules:
- IPv4 uses 8-bit binary numbers
- Maximum value of 8 bits = 255
- 258 cannot be represented in 8 bits
So even though 158.63.258.200 looks legitimate, it violates IPv4 standards.
Why Does 158.63.258.200 Appear in Logs or Searches?
Despite being invalid, 158.63.258.200 still appears in real-world systems. Here are the most common reasons:
Data Entry Errors
Someone manually typed an IP address incorrectly, adding “258” instead of a valid number.
Software Parsing Bugs
Applications that extract IP addresses from logs or headers may incorrectly split or merge values, leading to malformed addresses.
Corrupted Log Files
Log corruption or encoding errors can cause numbers to shift or merge incorrectly.
Placeholder or Test Data
Developers sometimes use fake IPs for testing, and 158.63.258.200 may appear as a placeholder.
Security Obfuscation
Some systems intentionally store invalid IPs to mask real user data or prevent tracking.
Is 158.63.258.200 Dangerous?
No — 158.63.258.200 is not dangerous by itself.
Because it is not a valid IP address:
- ❌ It cannot attack your system
- ❌ It cannot connect to servers
- ❌ It cannot belong to a hacker or botnet
- ❌ It cannot be geolocated
However, its presence may indicate an issue, such as:
- A logging or parsing bug
- Data corruption
- Poor validation in a form or application
- A misconfigured network tool
Can 158.63.258.200 Be Traced or Looked Up?
No. Since 158.63.258.200 is invalid, the following actions will fail:
- WHOIS lookup ❌
- IP geolocation ❌
- Reverse DNS ❌
- ASN lookup ❌
- Abuse database search ❌
Any tool claiming to provide real data for this address is either:
- Guessing
- Misconfigured
- Returning cached or fabricated results
Common Situations Where 158.63.258.200 Appears
Here are some real-world scenarios where this value may appear:
Web Server Logs
Misparsed headers or corrupted log entries may result in invalid IP addresses.
Security Tools
Firewalls or SIEM tools may log malformed connection attempts.
Data Imports
CSV or JSON imports sometimes misalign fields, resulting in invalid IP addresses.
Application Bugs
Incorrect IP validation logic may allow values greater than 255.
Manual Input Errors
Humans often mistype IP addresses during testing or configuration.
How to Handle 158.63.258.200 Properly
If you encounter 158.63.258.200, here’s what you should do:
Validate the Source
Check where the value came from:
- Log file?
- Database?
- User input?
- API response?
Reject or Flag It
Your application should reject IPs whose octets exceed 255.
Search for Nearby Valid IPs
Often, the intended address is close, such as:
- 158.63.25.200
- 158.63.28.200
- 158.63.2.58
Improve Input Validation
Use regex or IP validation libraries to prevent future occurrences.
SEO & Cybersecurity Perspective on 158.63.258.200
From an SEO or analytics standpoint, 158.63.258.200 has no real tracking value. However, it can indicate:
- Bot misbehavior
- Fake traffic
- Corrupted analytics data
- Logging misconfigurations
From a cybersecurity perspective:
- It is not a threat
- It does not represent an attacker
- It may indicate data integrity issues
Difference Between Valid and Invalid IP Addresses
| Format | X.X.X.X | X.X.X.X |
| Octet Range | 0–255 | ❌ 258 |
| Routable | Yes | ❌ No |
| WHOIS Lookup | Yes | ❌ No |
| Real Device | Possible | ❌ Impossible |
Final Thoughts on 158.63.258.200
The 158.63.258.200 IP address may appear legitimate, but in reality it is mathematically invalid and non-routable. Its appearance usually points to a technical issue rather than a real network entity.
You May Also Read: 192. 168. 101. 23:5244: A Guide to Secure and Efficient Private Networking